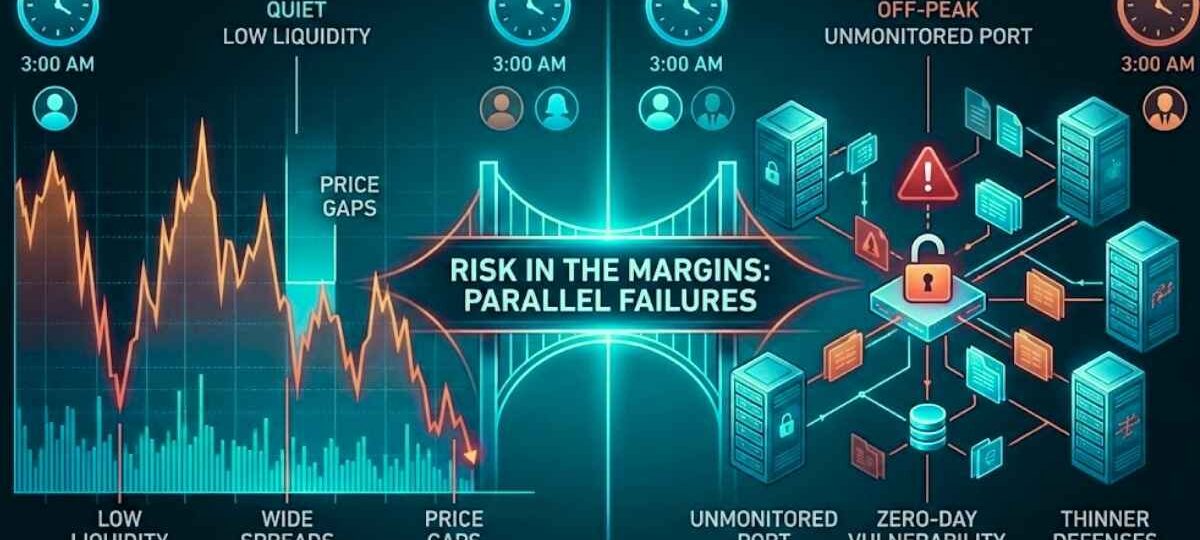
In both financial markets and digital security systems, the most important failures rarely happen under normal circumstances. They emerge in the margins, such as late hours, few participants, and moments when oversight is weaker. In online financial trading, this environment is known as low liquidity, meaning there are few participants and there is not much money moving around. In cybersecurity, it is the gap between controls, the unmonitored port, the unpatched zero-day vulnerability, or the off-peak hour when defenses are much thinner than usual. Below, we will discuss how understanding these two worlds reveals more than just correlations and why it is so important to learn lessons from other sectors in your career, be it cybersecurity or financial trading.
Liquidity as the Security Layer of Financial Markets
Liquidity is the market’s main shock absorber layer. When many participants are actively trading, there are always traders and participants who are willing to buy an asset or sell it at the current price, making the experience smooth and convenient for everyone. When liquidity thins, this buffer disappears, and even small orders can move prices sharply, spreads tend to become wider, and execution quality degrades.
This is the environment where financial markets might become riskier to enter, especially foreign exchange or Forex markets (FX). Low liquidity FX trading during periods such as session overlaps, ending, holidays, rollover hours, or unexpected news gaps are created when fewer participants are willing to buy or sell. This is similar across financial markets such as stocks and even cryptocurrencies. In these moments, the market’s defenses are weaker, and traders are exposed to different types of risks than usual.
Cybersecurity has a near-identical concept. A well-monitored network during business hours, with active logging and staff on duty, is usually very resilient. The same network at 3 a.m., during a maintenance window or holiday, is much more vulnerable, as there might not be enough stuff around to correct bugs or ensure stable working conditions. Since response capacity to emergencies is reduced, there is a latency in detection, reaction, and liquidity, which becomes an exploitable surface.
Gaps Are Not Accidents; They Are Structural
In financial trading, gaps are often described as surprises, price jumps, and skipped levels, leaving many orders unfilled. In reality, gaps are structural outcomes of order-book imbalances caused by low liquidity. If no one is willing to trade at an intermediate price, the market moves to the next available price level.
Security gaps work similarly. A vulnerability is not merely a bug; it is an absence of resistance. When an attacker encounters no effective control between unauthenticated and authenticated, unprivileged to privileged, the system gaps form.
In both cases, the gap is created by:
- Few traders or few monitoring processes
- Asymmetric information when one side knows more
- Delayed response creates latency in fills or alerts
Neither markets nor systems fail continuously, and there are moments when these gaps are more likely to occur, giving traders and cybersecurity teams an important advantage to plan smart responses and increase security.
Timing as an Exploit
Experienced traders are masters in timing markets, meaning they know that when you trade can matter more than what you trade. Entering a trading position during a high-liquidity London-New York overlap is fundamentally different from entering during the Asian session slow periods, minutes before market close, or on a Friday.
Ethical hackers think the same way. Penetration testing is not just about where the system might be weak, but when. Updates, backups, shift changes, and incident-response handoffs are the main windows to attack. The vulnerability may exist at all times, but is most exploitable when oversight is minimal. This is the main reason why flash crashes, stop-hunts, and abnormal price spikes occur during exactly low liquidity. It is also why some of the most damaging cyber attacks happen outside peak operational hours. Reduced participation amplifies impact.
Stop-Losses Versus Intrusion Detection Systems
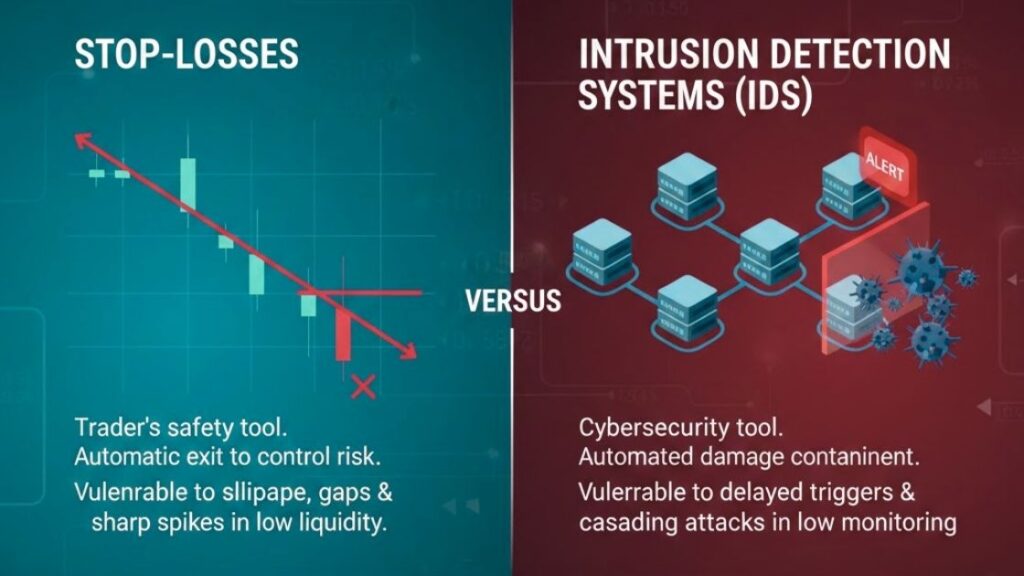
Stop-loss orders are a trader’s safety tools. They enable automatic exits to control the risk, which close open trades automatically when the price moves against it at some distance. During low liquidity market periods, slippage is higher, and when combined with gaps and sharp spikes, it is much easier to get stopped out.
Intrusion detection systems (IDS) serve similar purposes in cybersecurity. They are automated tools meant to contain damage. However, during low monitoring periods, these systems can trigger too late or be overwhelmed by cascading attacks.
As a result, in both domains, automation without context can magnify losses. Stops trigger because liquidity is nearly absent, not because the tool is bad, and alerts fire because thresholds are crossed, not because the attack is contained.
Key Takeaways
The parallels between cybersecurity and financial trading are significant. Here is where the main intersection points lie:
- Liquidity is a shock absorber – In markets, high liquidity ensures smooth trading, while in cybersecurity, increased monitoring decreases vulnerability.
- Structural gaps – Both trading and security gaps arise from imbalances in participation, information asymmetry, and delayed responses.
- Timing as an exploit – Just as traders target low-liquidity periods for advantage, attackers exploit off-peak hours, maintenance windows, or shift changes when defenses are low.
- Automation pitfalls – Stop-loss orders in trading and IDS in cybersecurity can both fail or worsen during low-liquidity or low-monitoring hours.
See Also: How Do Zero-Day Attacks Happen?