Understanding the nuances of digital security is crucial. You, as a professional navigating this complex terrain, must be acutely aware of pharming—a sophisticated cyber attack that subtly redirects users from legitimate websites to fraudulent ones without their knowledge. This article delves into the mechanics of pharming, examining its implications and strategies for prevention. By gaining a comprehensive understanding of this insidious threat, you can better protect your organization and its assets from potential harm. Join us as we dissect the intricacies of pharming and arm yourself with the knowledge to safeguard your digital environment.
Pharming Meaning and Definition
Understanding Pharming
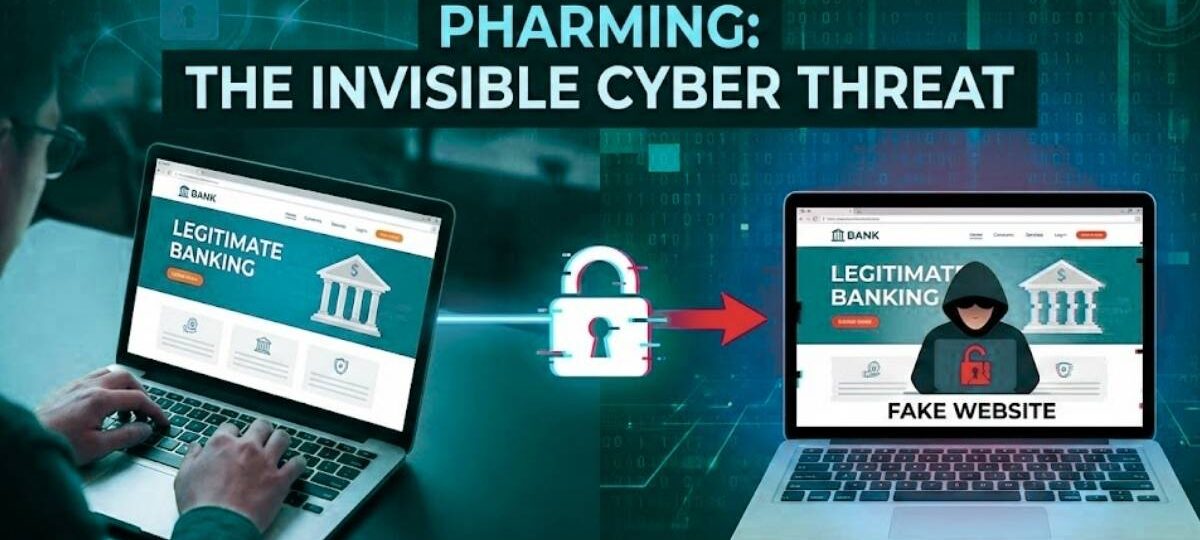
In the realm of cybersecurity, pharming represents a sophisticated and insidious threat to internet users. At its core, pharming is an attack that secretly redirects users from legitimate websites to fraudulent ones to steal sensitive information, such as login credentials or financial data. This redirection is achieved without the user’s knowledge, making pharming notably more covert than other types of online fraud.
A defining feature of pharming is its exploitation of vulnerabilities within the Domain Name System (DNS). Attackers may corrupt DNS tables through various means, most commonly via DNS poisoning or malware deployment. By altering the DNS configurations, these cybercriminals can seamlessly redirect traffic from the authentic website to their malicious counterpart.
Types of Pharming Attacks
Pharming attacks generally fall into two categories:
- DNS-based Pharming: This occurs when attackers compromise a DNS server, altering it to redirect multiple users’ requests to fraudulent sites.
- Host-based Pharming: This involves directly manipulating a victim’s host files or router settings, rerouting specific web requests to malicious domains.
Pharming poses a significant risk, particularly to users of e-commerce and online banking services, as users are typically unaware their data is being intercepted and misused. Effective prevention strategies include maintaining robust antivirus software, utilizing secure connections such as HTTPS, and employing two-factor authentication to shield personal information from these deceptive attacks.
How Pharming Works in Cyber Security
Exploitation Methods
In the realm of cyber security, pharming employs cunning exploitation techniques that bypass traditional user engagement. A prominent method involves DNS poisoning, where attackers manipulate the Domain Name System to redirect users from legitimate websites to counterfeit ones. By altering DNS tables on a server, they cause multiple users to unwittingly visit malicious sites. Another common tactic is malware-based pharming. Here, malicious software changes the host file on a victim’s device, redirecting traffic to impostor websites that closely mimic legitimate ones. These methods underscore the insidious nature of pharming, which operates silently and largely unnoticed by users.
The Invisible Threat
Pharming is particularly dangerous because it does not rely on user mistakes, such as clicking on a malicious link or opening a phishing email. This passive nature means that even diligent users who manually type URLs into their browsers may fall victim. Once an unsuspecting user is redirected, attackers can harvest sensitive information such as login credentials or financial data, often using these details for identity theft or financial fraud.
Recognizing and Mitigating Pharming
Recognizing a pharming attack can be challenging, yet key indicators include being redirected to unfamiliar websites or observing discrepancies on familiar sites. Maintaining strong cyber defenses is crucial in mitigating these threats. Establishing routine security practices like using reputable antivirus software, enabling two-factor authentication, and employing a secure DNS server are vital. Vigilant internet browsing practices and keeping systems updated further bolster defenses against this deceptive form of cybercrime.
Types of Pharming Attacks and Examples
DNS-Based Pharming
At the core of DNS-based pharming lies the manipulation of the Domain Name System (DNS). Attackers exploit vulnerabilities within this web-traffic directory to stealthily redirect users to fraudulent websites. This type of attack can manifest through DNS cache poisoning—where malicious data is inserted into a DNS resolver’s cache—or DNS server compromise, wherein a hacker takes control of the server itself. A significant example is the 2007 DNSChanger malware attack, which corrupted DNS settings on victim devices, funneling them to counterfeit websites laden with deceitful advertisements and phishing traps. In such scenarios, the user remains unaware of the ongoing deceit, heightened by the absence of malicious prompts often associated with phishing attacks.
Host-Based Pharming
Host-based pharming attacks leverage the more localized aspect of DNS manipulation. Here, attackers target the host file on a user’s device, redirecting it from legitimate sites to identical fake ones. By altering host files, cybercriminals can craft scenarios where entering the correct URL results in landing on counterfeit platforms. This technique was notably employed in a Venezuelan attack targeting over 50 banks, where login credentials were harvested surreptitiously. Unlike DNS-based attacks, host-based methods often require direct access to the device or distribution of malware to execute the redirection.
Pharming vs. Phishing: What’s the Difference?
Understanding Pharming and Phishing
In the ever-evolving landscape of cyber security, distinguishing between pharming and phishing can be pivotal to protecting sensitive information. While both are malicious tactics used by cyber criminals, they employ different methods to achieve their nefarious goals.
Pharming is a technique that manipulates the Domain Name System (DNS) to silently reroute users from genuine websites to fraudulent ones. This attack often occurs when DNS settings are compromised, either on a user’s device or on a DNS server itself. As a result, even if the correct website address is entered, users unknowingly land on a replica, designed to harvest personal information. Detecting this type of attack can be challenging, as everything on the surface appears normal to the unsuspecting user.
Conversely, phishing predominantly involves social engineering, where attackers trick individuals into divulging sensitive data. Commonly executed through deceptive emails or fake websites, it preys on human error. Unlike pharming, phishing requires user interaction, such as clicking a link or responding to a misleading email. The tell-tale signs of phishing often include poorly crafted messages or urgent requests for personal details.
Key Differences Between the Two
While both pharming and phishing pose significant risks, the core difference lies in their execution. Pharming impacts users passively, redirecting them without their knowledge, making it particularly insidious. On the other hand, phishing demands active participation from the victim, exploiting trust through crafted deceit. Pharming can potentially affect numerous users simultaneously across a network, whereas phishing generally targets individuals one at a time.
To mitigate risks, employing security measures such as updated DNS protection and vigilant user education can provide robust defenses against these cybersecurity threats. Understanding these distinctions is vital for strengthening your digital defenses and maintaining the integrity of personal and sensitive information.
How to Protect Yourself Against Pharming
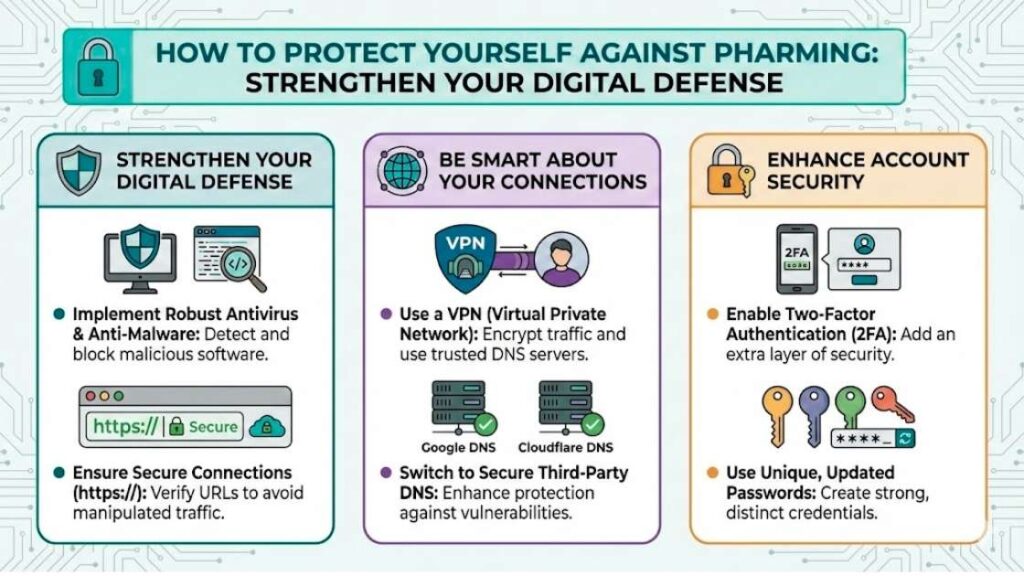
Strengthen Your Digital Defense
To navigate the digital world safely, proactively safeguarding against pharming attacks is essential. Start by implementing robust antivirus and anti-malware software capable of detecting and blocking malicious activities. This foundational step can thwart attempts to install harmful code on your devices. Always ensure that your browsing occurs over secure connections, denoted by URLs beginning with “https://”—a simple yet effective way to avoid falling prey to manipulated DNS traffic.
Be Smart About Your Connections
Using a Virtual Private Network (VPN) can further shield your digital movements. By filtering your internet traffic through trusted DNS servers, VPNs greatly reduce your exposure to DNS cache poisoning, a common vector in pharming schemes. Additionally, consider switching to more secure third-party DNS services like Google DNS or Cloudflare DNS that offer enhanced protection against such vulnerabilities.
Enhance Account Security
On a more personal security front, enable two-factor authentication (2FA) wherever possible. This additional security layer serves as a formidable barrier against unauthorized access attempts. Coupling 2FA with frequently updated, unique passwords for each of your accounts and devices adds yet another vital layer of protection against the persistent threat of pharming.
Signs of a Pharming Attack: How to Tell If You’re a Victim
Unusual Website Behavior
Spotting a pharming attack begins with noticing subtle changes when you visit familiar websites. Pay attention to any unusual behavior, such as different layouts, altered logos, or unexpected prompts requesting personal information. These red flags often signal that you may have been redirected to a fraudulent site. Beware if you encounter unexpected pop-ups demanding sensitive data, as these could be signs of a malicious actor attempting to harvest your information without your consent.
Suspicious URLs and Redirects
Detecting pharming attacks also involves scrutinizing web addresses. Be wary of URLs that feature extra characters or misspellings, as these are common indicators of malicious sites. A critical sign includes the absence of “https” in web addresses, or SSL certificate errors, suggesting you’ve been rerouted to a dangerous website potentially due to compromised DNS settings. If you experience inconsistent redirection when entering a website’s URL, it might be time to investigate further.
Anomalies in Account Activity
Unusual account activities can signal a successful pharming attack. If you notice unexplained transactions or changes in your settings, your credentials might have been compromised. Keep a vigilant eye on your accounts for any unauthorized activities, as early detection can prevent significant financial and reputational harm. Regularly monitoring these elements can mitigate the risk of falling victim to such sophisticated cyber threats.
FAQs

What Makes Pharming Distinct from Phishing?
While both pharming and phishing are forms of cyberattacks aimed at stealing sensitive data, their methods differ substantially. Pharming does not require user interaction to direct victims to fraudulent websites; instead, it manipulates technical systems such as DNS settings or uses malware to automatically reroute users. In contrast, phishing often employs social engineering tactics, like misleading emails, to lure individuals into voluntarily providing their information. This distinction underlines the importance of vigilance and robust cybersecurity practices to mitigate these threats.
How Do Pharming Attacks Occur?
Pharming attacks are executed through several methods. DNS poisoning is a common approach where attackers corrupt DNS records to redirect traffic to deceptive sites. Host file modifications represent another technique, where malware alters a device’s DNS settings. Additionally, setting up rogue DNS servers can trick users into visiting counterfeit web pages without their knowledge. To counteract pharming, employing updated security software and multi-factor authentication is highly recommended for enhanced protection.
What Protective Measures Can Be Taken?
Mitigating pharming attacks involves a multi-faceted approach. It is crucial to practice vigilant digital hygiene, such as verifying URLs and implementing secure DNS services. Regularly updating systems and security patches, combined with two-factor authentication, adds layers of defense. Businesses and individuals should engage in security training to remain aware of evolving threats. By prioritizing these preventive steps, one can effectively shield valuable personal and corporate information from the impacts of pharming and similar cyber threats.
Conclusion
In the ever-evolving landscape of cyber security, understanding the intricacies of pharming is crucial. As you’ve seen, this sophisticated threat bypasses traditional defenses, redirecting users to malicious sites without their knowledge. By implementing robust security measures, staying informed about emerging threats, and fostering a culture of vigilance, you can effectively mitigate the risks associated with pharming. Remember, the digital world is not without its dangers, but with knowledge and proactive strategies, you are well-equipped to protect your digital assets. Stay vigilant, stay informed, and you will remain a step ahead in the fight against cyber threats.