As cyber threats become increasingly sophisticated, understanding User Behavior Analytics (UBA) emerges as a pivotal strategy for strengthening your cybersecurity framework. This article delves into the essentials of cyber UBA, providing you with a comprehensive overview of its role in detecting anomalies and mitigating risks. By harnessing the power of UBA, you can proactively identify potential threats and protect your organization’s valuable data assets. Join us as we explore how embracing UBA can transform your approach to cybersecurity, ensuring robust defense against ever-changing digital threats.
What Is User Behavior Analytics (UBA) in Cybersecurity?
Defining User Behavior Analytics
User Behavior Analytics (UBA) is a cutting-edge cybersecurity technique that scrutinizes patterns in user activity to detect anomalies that may signal potential threats. By analyzing user behaviors such as login attempts, resource access, and data downloads, UBA helps organizations establish a baseline of normal activity. When deviations occur, these analytics raise alerts, making it possible to identify insider threats and fraud before they unfold.
How UBA Works
UBA collects data from various sources, including credentials and network traffic, using machine learning to analyze and model user behavior. This approach enables businesses to anticipate threats by identifying deviations from expected patterns, even in complex cybersecurity environments. For instance, repeated abnormal login attempts or unusual data transfer activities are flagged for investigation, helping to thwart potential security breaches.
Benefits of UBA
By focusing on human behavior, UBA enhances threat detection capabilities beyond traditional security tools. It provides businesses with an advanced layer of defense against sophisticated cyberattacks, detecting insider threats and unauthorized access swiftly. Consequently, organizations can mitigate risks effectively, thereby preserving data integrity and ensuring compliance with cybersecurity regulations. As UBA adapts to evolving threats, it serves as a vital component in comprehensive security strategies for modern enterprises.
How UBA Works: A Technique Overview
Establish Baselines
User Behavior Analytics (UBA) functions by collecting data from various sources like log files, network traffic, and application usage. It establishes a baseline of typical user behavior patterns for each individual. By doing so, it creates a reference point of “normal” behavior, which is critical for spotting anomalies. When deviations from the baseline are detected, UBA can identify potential security threats like insider anomalies or unauthorized access attempts.
Detection and Response
UBA utilizes machine learning algorithms to analyze user activities in real-time, enabling the system to detect deviations from established baselines efficiently. Such anomalies could indicate various threats, such as compromised accounts or malicious insiders. This detection capability is pivotal for cyber UBA as it allows organizations to respond promptly to potential risks and mitigate damage. Enhanced with risk scoring, security teams can prioritize alerts and ensure swift action.
UBA Use Cases: Enhancing Cybersecurity for Businesses
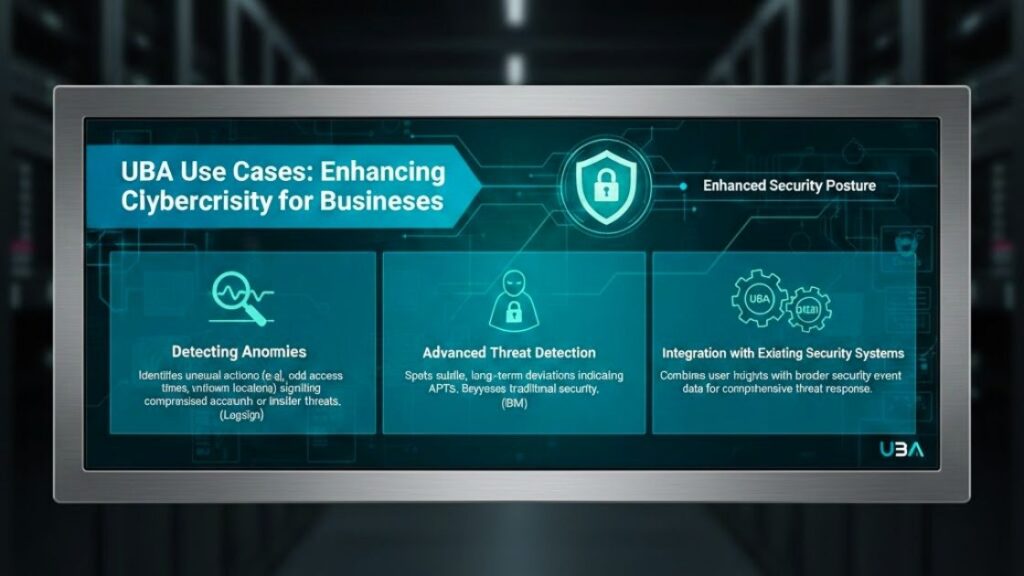
Detecting Anomalies
User Behavior Analytics (UBA) excels at detecting anomalies in user behavior, which is crucial for identifying potential security risks. By establishing a baseline of normal behavior, UBA can identify when a user exhibits unusual actions, such as accessing sensitive data at odd hours or from unknown locations. Such deviations often signal compromised accounts or insider threats, helping organizations respond promptly to potential breaches.
Advanced Threat Detection
UBA is effective in identifying advanced persistent threats (APTs). By analyzing user behavior over time, UBA spots subtle and long-term deviations that might indicate a covert attack. This capability enables businesses to detect threats that could bypass traditional security measures, offering a more nuanced understanding of cybersecurity risks (IBM).
Integration with Existing Security Systems
UBA enhances cybersecurity by integrating seamlessly with existing security systems, such as Security Information and Event Management (SIEM) systems. This integration allows businesses to achieve a comprehensive security posture by combining granular user-level insights with broader security event data, augmenting the ability to detect and respond to threats in real-time.
UBA Versus UEBA: Understanding the Differences
User Behavior Analytics (UBA)
UBA, or User Behavior Analytics, focuses exclusively on monitoring and analyzing the actions of human users within a network. It identifies anomalies that could signal malicious activities, such as unauthorized data access or unusual login locations. UBA provides businesses with insights into user-related threats, helping to prevent potential data breaches.
User and Entity Behavior Analytics (UEBA)
UEBA extends beyond merely observing user actions, embracing a broader scope by including entities like servers, devices, and applications. By integrating data from various sources and using machine learning, UEBA detects intricate threats involving both human and machine actors. This enhanced functionality makes UEBA more robust and comprehensive in safeguarding business networks.
What Is the Difference Between UBA and EDR?
Understand the Core Focus
While both Cyber User Behavior Analytics (UBA) and Endpoint Detection and Response (EDR) serve to enhance cybersecurity, they do so with distinct focuses. UBA primarily analyzes the behavior of users within the network to identify anomalies that might signal potential security threats. In contrast, EDR zeroes in on individual devices, detecting and addressing threats like malware and unauthorized access at endpoints such as laptops or servers.
Integration for Enhanced Security
Combining UBA and EDR provides a more comprehensive cybersecurity strategy. UBA offers insights into user activities, allowing for the identification of insider threats, while EDR focuses on external attacks. By integrating both, businesses can achieve a robust defense system, enhancing their overall security posture. This dual approach not only detects anomalies but also responds promptly to potential threats, fortifying the organization’s defenses.
UBA Challenges: Overcoming Common Obstacles
Fine-Tuning for Accuracy
One of the primary challenges with implementing cyber UBA is managing false positives—alerts generated from normal behavior incorrectly flagged as threats. Fine-tuning UBA models and thresholds is crucial to minimizing these distractions while ensuring effective threat detection.
Managing Data Privacy
Dealing with large volumes of data raises privacy concerns. Establishing clear data governance policies will help address these issues without hindering the data collection necessary for robust UBA implementation.
Conclusion
In conclusion, grasping the fundamentals of Cyber User Behavior Analytics (UBA) is pivotal for safeguarding your business in today’s digital landscape. By leveraging UBA, you can enhance your cybersecurity measures, enabling proactive threat detection and efficient incident response. As cyber threats evolve, investing in UBA provides a strategic advantage, helping you understand user behavior patterns and identify anomalies before they escalate into significant breaches. Ultimately, integrating UBA into your cybersecurity strategy not only fortifies your defenses but also fosters a culture of vigilance and resilience. Embrace this technology to protect your business’s integrity and ensure its sustainable growth.
See Also: Cyber Security Development Program Associate – 2026